By Robert McDermott
President & CEO, iCoreConnect (LDA/LDS endorsed company)
No one likes to be manipulated, yet we are subjected to invasive tactics in our email to get us to click a link, give access to sensitive data or share confidential information. These aren’t just spam emails. Cybercriminals are using an email approach called ‘social engineering’ designed to feel and look familiar to quickly gain your trust.
Dental and medical practices are among the most vulnerable to cyber attacks. Protected Health Information (PHI) is a high dollar commodity, selling for hundreds of dollars per record. Practices may also be crippled by cybercriminals who hold your data for a high ransom.
Here’s how cybercriminals socially engineer their attacks. They tend to gather information about your industry, your business, and even your employees. Once they have enough information, they send out a targeted email campaign, called phishing. The email is just close enough to a real email that the recipient may trust its legitimacy and take a requested action, like opening an attachment or clicking a link.
Let’s look at one specific example. In a phishing attempt impersonating Amazon, cybercriminals claim a package was shipped to the wrong address and are requesting a call back to fix the issue. If you take action, those bad actors immediately work to steal money, compromise your data and perhaps cripple your practice operations.
Here are four ways you can quickly determine when email has been socially engineered to trick you.
1. Can you verify the sender? Does the name or email address look suspicious?
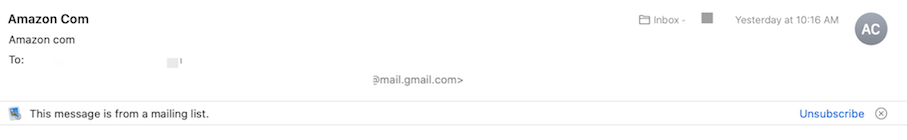
Notice the sender address on the left is similar to the actual “Amazon.com” address. Whether you’ve received a questionable email from an apparent colleague or friend, or an attempt like this one, you’ll notice that the email address may closely resemble a known company or domain but something is always amiss. The big differences include a slight altering of name or spelling, spacing or punctuation issues and/or omitting of a few characters.
2. Look for generic greetings, incorrect spelling and poor grammar.
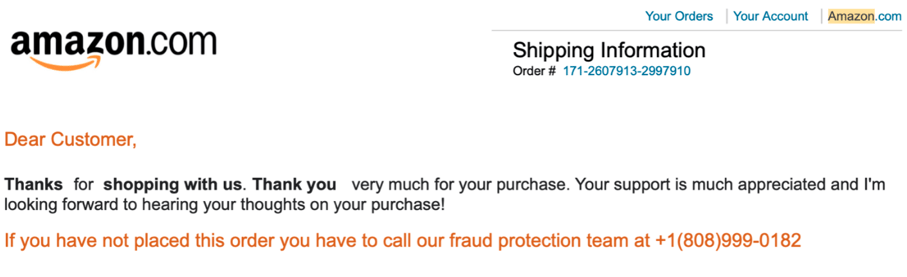
Dear Customer/Sir or Madam, this email is a trick.
Well, they may not be that direct, but the “Dear Customer” or “Sir and Madam” types of greetings may be a tip off. Most legit companies will insert your name in the greeting. In this phishing attempt, like most others, there are spacing issues in the body of the email, repetitive content and missing punctuation.
3. Be wary of unusual information.
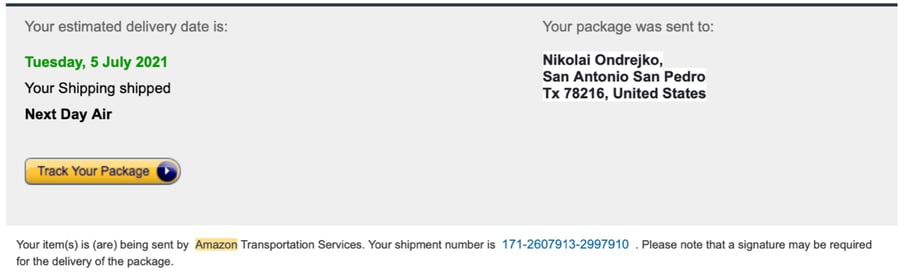
Check out the delivery address. It says ‘San Antonio San Pedro’ which isn’t a real place. It’s good to ask yourself questions when something feels off. For instance, why would a known vendor share another person’s personal information with you?
4. Don’t click the links.
In the case of the Amazon spoof, the links take you to Amazon, but not to your supposed order. The goal of this, and many phishing attacks, is to get you to call a phone number or click an attachment or often a link containing malware. The attack attempt here drives you to call them. That’s when they will likely ask you to verify credit card or bank account information. Clicking a link can install malicious bugs to steal your data, like PHI, or shut down your entire practice.
In addition to educating your staff to identify suspicious emails, make sure your practice is using a truly HIPAA-compliant secure email, with multi-layered security, to prevent phishing attempts from even making it to your inbox. A high encryption level of 2048-bit and a built-in user verification process will make your practice email almost impossible for a cybercriminal to access.
Awareness, staff education and fully HIPAA-compliant email will keep your practice and patient information safe from those who stand to profit from an unintentional click of a link or phone call to a cybercriminal.
LDA endorses iCoreExchange secure, HIPAA-compliant email. iCoreExchange not only meets or exceeds every compliance and security requirement, it also allows you to attach as many large files as you want to any single email. Speed up your workflow, protect patients and your practice.